Shedding light on dark social traffic
A lot of great articles have been written about dark social traffic since 2013, but it’s still an issue that impacts traffic data collection on a daily basis for all web analytics tools (even Google analytics). If you see a high percentage of direct traffic (especially for pages with long URLs, which are difficult to type), you should spend some time to go through this article.
A very quick description of the term “dark social” and the issues it comes with is the following:
Dark social is used to group all traffic coming to a website, from Social networks, native mobile applications, chat clients or email but fails to be classified correctly by a Web analytics applications. This type of traffic usually appears as direct traffic. This happens either to protect user’s privacy or because some of these applications are not exposing information in the same way web browsers do. So at the end it’s just private referral traffic that’s harder to track, as it comes back without referral data attached.
For more information about dark social you can check the links below:
- [eConsultancy] The rise of dark social and everything you need to know
- [Chartbeat] The state of dark social in 2014
- [The Atlantic] We have the history of the web wrong
- [LunaMetrics] Direct visits in Google analytics – A wolf in sheep’s clothing
How much impact does “dark social” have on my website?
According to folks from, RadiumOne more than 80% of online shares is happening through dark social!
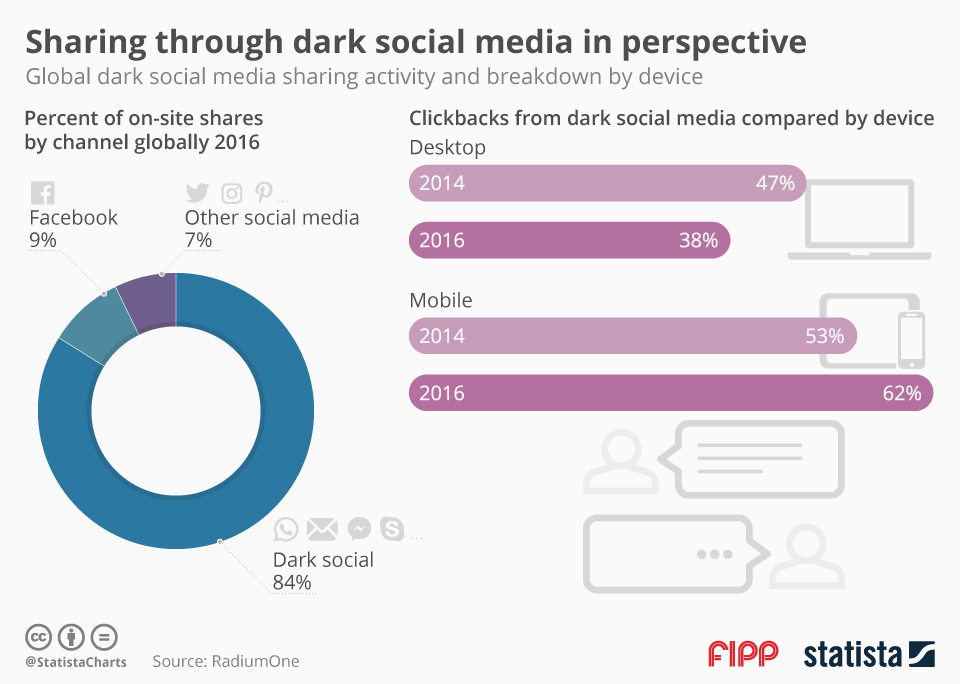
Another way to understand the impact on your website, is to check your analytics platform for direct traffic on very long URLs. It’s almost impossible that someone would visit a URL like http://tzamtzis.gr/2017/web-analytics/reasons-to-invest-in-analytics/ just by typing it on his browser and the amount of visitors who bookmarked your URL or pasted it in their browser will probably not be that high. This is probably a URL that was accessed through a dark social traffic source.
There’s a great article from Chris Breaux in Chartbeat’s blog, explaining the most common sources of dark social traffic. He also tested the sources and found the cases where referrer information is not passed along to the target page of a link:
| Referrer Passed? | |||
| Tumblr | |||
| Gmail | |||
| IM/Text |
* Sometimes when opening a link in a new tab referrer is not passed along
How to fix this issue?
Make it very easy for your visitors to include referral data before sharing content from your website
- Implement social sharing buttons that will also include a tracking code URL parameter in the URL being shared. Make sure that these buttons are easy to use and make the sharing process faster, otherwise it doesn’t make a lot of sense for the visitor to use them.
- Include referral data on all the URLs of your website. This way if anyone decides to copy-paste and share one for your pages, he will probably also include valuable information about the visit. An advanced option available is a GA plugin called DirectMonster.js by LunaMetrics. (If you’d like to see that in action, Mashable seems to be using a similar approach: Sample mashable article link )
- Use campaign tracking codes when sharing links. If you are using GA you can use this builder to create campaign links compatible with GA
- Decode the browser’s user agent to understand the correct source of traffic (More details below).
Track visits by user agent
The user agent string, is a short text property that is available for every browser. This property holds details about the browser, the operating system and the device used to browse the web. There are bits and pieces available in most user agent strings, allowing us to get more details about the correct traffic source, even for cases like the ones mentioned above. So when you set the rules that classify your traffic in marketing channels, be sure to include the following ones, to make you tracking even more accurate and minimize the impact of dark social traffic.
Facebook mobile apps
To identify traffic from a facebook mobile app you can look for one of the following values in the user agent strings:
- FBAN/
- FBAV/
- FBBV/
- FBDV/
- FBMD/
- FBSN/
- FBSV/
- FBSS/
- FBLC/
- FB4A;
A few sample facebook user agent string including these values:
Mozilla/5.0 (iPhone; CPU iPhone OS 10_3_1 like Mac OS X) AppleWebKit/603.1.30 (KHTML, like Gecko) Mobile/14E304 [FBAN/FBIOS;FBAV/91.0.0.41.73;FBBV/57050710;FBDV/iPhone8,1;FBMD/iPhone;FBSN/iOS;FBSV/10.3.1;FBSS/2;FBCR/COSMOTE;FBID/phone;FBLC/el_GR;FBOP/5;FBRV/0] Mozilla/5.0 (iPhone; CPU iPhone OS 10_3_1 like Mac OS X) AppleWebKit/603.1.30 (KHTML, like Gecko) Mobile/14E304 [FBAN/FBIOS;FBAV/92.0.0.46.70;FBBV/57733420;FBDV/iPhone8,1;FBMD/iPhone;FBSN/iOS;FBSV/10.3.1;FBSS/2;FBCR/vfGR;FBID/phone;FBLC/el_GR;FBOP/5;FBRV/0] Mozilla/5.0 (Linux; Android 4.4.4; One Build/KTU84L.H4) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/33.0.0.0 Mobile Safari/537.36 [FB_IAB/FB4A;FBAV/28.0.0.20.16;]
Twitter mobile apps
To correctly identify traffic coming from a twitter mobile app, you can look for the following value in the user agent string:
A few sample user agent strings, that were captured using this rule:
Mozilla/5.0 (iPhone; CPU iPhone OS 9_3_5 like Mac OS X) AppleWebKit/601.1.46 (KHTML, like Gecko) Mobile/13G36 Twitter for iPhone Mozilla/5.0 (Linux; Android 7.0; E5823 Build/32.3.A.2.33; wv) AppleWebKit/537.36 (KHTML, like Gecko) Version/4.0 Chrome/58.0.3029.83 Mobile Safari/537.36 TwitterAndroid
Other apps
This list can go on forever but it gets very time consuming to find differences in user agent string for less known apps. For me the best approach is to start capturing the user agent string in your web analytics platform, using the following JS property:
navigator.userAgent
Once you started capturing user agents, you can start looking into all the values classified as “Direct” traffic. Your will try to find patterns you could potentially classify as a different channel.


